
Joe Pulizzi has been a content marketer before content marketing had a name. While working at a media company in the Custom Publishing department, he had dreams of starting a small business, which he eventually did in 2007 by starting a blog about content marketing.
Fast forward 3 years later and he had built Content Marketing Institute, which is well-known today as a source of content marketing thought leadership, training, events and consulting.
Today, Joe is joined by many other companies who built their businesses aided by the power of creating an audience first through content marketing, such as CopyBlogger Media, Social Media Examiner, Moz and even our very own agency, TopRank Online Marketing.
Being the curious type, Joe wanted to know more about the paths which other businesses had taken in their journey to success through content marketing, so he did some asking around. The interesting thing he found was that when boiled down, there were remarkable similarities between these businesses in terms of the process and steps they had taken, which led Joe to the conclusion that there is a consistent formula for content marketing success.
In his session at the recent Authority Rainmaker conference, Joe shared six steps businesses should follow if they want to join the ranks of those getting incredible value from content marketing.
#1 Find Your Content Sweet Spot
It’s hard to make people care about a topic unless you care about it yourself and even harder to hold their attention if you don’t know what you’re talking about. The most successful content comes from people who have identified both:- Their area of expertise: what they know
- Their passion: what they love
#2 Find Your Content Tilt
While it would be great if we could all only write about exactly what we wanted (your sweet spot), unfortunately that may not pay the bills without some tweaking. Successful content marketing means serving others first, not yourself, so if your content sweet spot doesn’t align with the needs and interests of your community, it likely isn’t going to attract many eyeballs (or wallets).Similar to expertise and passion, there may not be a perfect overlap between your sweet spot and what your community wants. Alternately, you may share your sweet spot with others who have well-established authority that would be tough to compete with.
Tilting your content means tweaking your focus so it aligns with an area of opportunity in the community that falls within your sweet spot. Even with the explosion of content on the internet today, there are still plenty of areas which aren’t being served effectively, or at all. If you can tilt your content focus to be the only one that serves the niche, or simply serves it better than anyone else, you can become an authority that attracts and audience and keeps them engaged all the way through to converting into customers.
The key is to be very specific, as this allows your content to be tightly targeted and specific to the needs of your niche community. As John Lydgate famously said, “you can please some of the people all of the time, you can please all of the people some of the time, but you can’t please all of the people all of the time.”
The goal for your content should be to please some of the people all of the time, so avoid broad content like a bad cold.
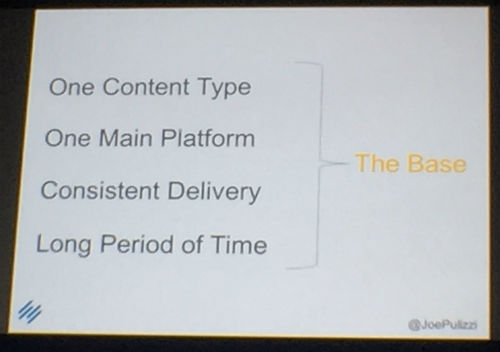
#3 Build Your Base
Before you can start to see business benefits from your content, you’re going to need a build a base audience. This takes time for everyone, so it’s important to be patient and set realistic expectations both for yourself and for your key stakeholders.Brian Clark (CEO of CopyBlogger media) built his base for over 15 months before seeing any monetary gains. Joe admits that when he started the blog that evolved into Content Marketing Institute, he had an audience of one (his mom). It took time for the experts to build a base and it will for you too.
In order to attract an audience, you need to create a content hub for them to go to. While you will need to promote and publish your content to a variety of destinations in order to get traction, your content base or hub is your primary platform where publishing takes place and it should be a place you own, like your blog or newsroom.
The reason why it’s so critical to own your content hub is that it’s insurance for the future. Like many businesses learned last year when Facebook drastically reduced the visibility of brand content without paid promotion, building your content hub on rented land is a recipe for disaster if the landlord decides to change the rules, raise the rent or evict you.
#4 Harvest Your Audience
While our primary focus so far has been to attract new eyes to our content, it’s important to remember to pay attention to retaining those eyes. The internet is awash in content these days and people have short attention spans, so it’s important to keep people coming back or they might forget you.The key to staying memorable with your audience is to maintain consistent regular touch points by converting them into subscribers. While it may not be the trendiest tactic in digital marketing, email lists are the gold standard when it comes to building a subscriber base. Joe strongly recommends prioritizing email far above social followers, as email tends to generate far better response rates and eventually revenue.
One of the best ways to keep your list growing is to make it dead simple to join. Prominent links on your site template, cross-linked in blog content and on your social channels are essential. Make sure to thoroughly test all your subscription forms as well as reduce required fields down to the bare essentials, as too many form fields are an absolute conversion killer.
While controversial, you should also consider using popup subscribe boxes. Joe was against these at first, but changed his tune when a test showed that popovers not only increased subscriptions but tended to bring in better qualified subscribers compared to the standard non-popup forms.
#5 Diversify Your Offerings
While you should never waver in your topic focus, it makes sense to branch out into multiple formats for your message, as this may help you to both reach new audience members and reinforce your authority among your existing subscriber base.Joe recommends pursuing a model of content diversification, which includes:
- Personal content:
- Blog
- Book
- Public speaking
- Business content:
- Digital
- In-person

#6 Monetize
“First build an audience, then monetize it”. For Joe and his team at Content Marketing Institute, their monetization comes in the form of consulting, training and events. Your revenue source(s) will likely be unique to your business, but you should always be on the lookout for new ways to monetize your content marketing.Although monetization is typically the last step in the audience building roadmap, you should never pass up opportunities along the way to get some monetary value from your content marketing. You may even come across revenue opportunities you never even considered at the outset.
Just make sure that you never cross the line of being pushy or dishonest with your audience in your attempts to monetize. The objective of content marketing is first and foremost to serve your community.
